Hello, my name is Shawn, and I have used weak passwords to protect important computer accounts and data…
Whew! now that I have that off my chest, I would like to share some thoughts on passwords with you. The primary audience for this post are the family members and friends for whom I provide computer tech support. My goal is to give you some simple guidelines for strong and easy-to-use passwords. I’m going to start by providing just a little background info. If you start to get bogged down in the background material please jump ahead the recommendation section.
Passwords 101
To intelligently select a strong password you need to have a rudimentary understanding of how computer systems store and use passwords. The most important thing for you to know is that any moderately secure computer system should not store your actual password. Instead, your password is processed through a one-way mathematical function (known as a cryptographic hash function) that generates a numeric key uniquely correlated to your password. Since the cryptographic hash function is one-way, it is essentially impossible to use the stored key to re-create your password. Incidentally, this is why a computer system administrator can’t look up a lost password for you.
I mention the cryptographic hash function to help you understand how thieves can break into your computer account. Since your password is not stored on the computer system the thief must either steal the password from you or they must “crack” your password by repeatedly trying different passwords. The purpose of strong passwords is to thwart such password cracking attempts. Passwords may be cracked via two basic methods (1) intelligent guessing, and (2) brute-force attacks.
The intelligent guessing method is called a dictionary attack. In a dictionary attack a sophisticated cracking program automatically tries passwords from a list (a dictionary) of likely passwords. Don’t be fooled by use of the word “dictionary” here, because the list of likely passwords has been painstakingly assembled by devious minds and includes far more than just words from Merriam-Webster. Not only will cracking software have dictionaries with all common passwords, but the software may also be configured to use dates, names, and words with a personal connection to you. Your goal is to select a strong enough password to defeat dictionary attacks and force the thief to resort to a brute-force attack.
In a brute-force attack the cracker is reduced to trying all possible password character combinations. Given enough time a brute force attack will succeed. Your goal is to make the attack take so long (i.e. many, many years) that it will no longer matter when the cracker succeeds. The best defense against a brute-force attack is a very long password composed of completely random characters selected from all character sets (i.e. lowercase, caps, numbers, and symbols).
The problem and a recommended solution
Long passwords composed of random characters are nearly impossible to remember and are typically difficult to enter. Also, common computer security protocols require you to change passwords every 60 to 90 days. These realities cause folks to gravitate towards weak passwords and/or to use the same password on multiple systems. I am proposing a system that will produce strong-yet-usaable passwords by combining a couple of clever ideas.
Idea # 1 random common words
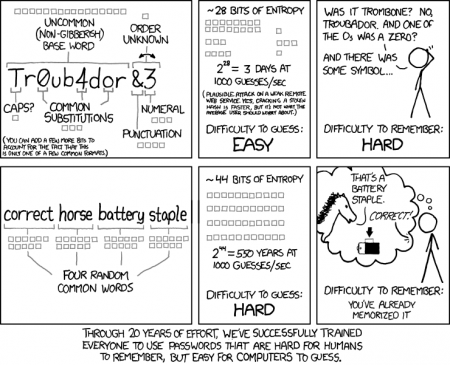
Randall Munroe, the genius behind xkcd, has a gift for communicating complex concepts with exceptional clarity and brevity. The following comic illustrates the shortcomings of common passwords and proposes a better solution.
Randall’s proposed solution uses a string of random common words to create a strong-yet-usable password. Breaking the long password into common word chunks makes it easy to remember and easy to type. As the comic suggests, you can develop a mental image/story to help you remember the word chunks of your password It is important for the word chunks to be as random as possible and unconnected to anything in your life. Online xkcd-style password generators are now available, but it is generally not advisable to accept passwords provided by others. A more secure password generation technique involves random selection of words from a paper dictionary. Geeks like me or the truly paranoid may find the diceware approach appealing.
Idea # 2 password padding
Steve Gibson of Gibson Research Corporation is a computer security expert. In a recent article, he makes a compelling argument for padding passwords to increase strength. He illustrates his point by comparing the relative merits of the following two passwords:
password 1: D0g..................... password 2: PrXyc.N(n4k77#L!eVdAfp9
Assuming that the cracker is forced into brute-force attack mode, the first password will take 95 times longer to crack than the second. I strongly recommend reading Steve’s article before you adopt his password padding approach. At a minimum, be sure to read the “One Important Final Note” section near the bottom of the page.
Steve’s solution highlights a key point. Despite what Hollywood would have you believe, password crackers must correctly guess the entire password. They can’t solve the puzzle one character at a time. It doesn’t work like Wheel of Fortune where correctly identifying one padding period will reveal all of the other padding periods. Remember that the cracker is testing sample passwords against keys created by the one-way cryptographic hash function.
Recommended solution: combine ideas # 1 and # 2
I recommend combining the two ideas to create your own password solution. Randomly select a batch of common, easy-to-remember words and intersperse some padding in a pattern of your own creation. Your padding pattern should include any types of characters not found in your random word chunks (i.e. caps, numbers, symbols, etc.). Using the examples shown above your password might look like:
correcthorsebatterystaple!1A
Please note that I am intentionally giving you a rather unimaginative padding example. It is important that you develop your own password creation recipe (i.e. algorithm). Do not use padding patterns or word/chunks suggested by others – particularly those that have been published online. It is virtually certain that cracking software dictionaries already include the “correcthorsebatterystaple” and “D0g…………………” passwords that Russell and Steve have published.
Final thoughts
Your carefully-generated strong password is only good as long as you keep it secret and secure from theft. Security experts advise against writing passwords down anywhere. As a practical matter, most of us need to write things down. If you do this please be security conscious – particularly if you are storing the passwords on your computer. For computer-based password storage I strongly recommend encryption with tools like KeePass or TrueCrypt.
KeePass and similar online password managers like LastPass include features for automatically generating strong, random passwords and automatically entering them into your various computer accounts. Personally, I don’t like this solution because it makes you entirely dependent on the password management software. If you don’t have access to your password management tool there is no way that you will be able to manually enter a long, random password that you are used to entering automatically. Additionally, I am uncomfortable trusting online entities like LastPass with all of my passwords.
Hard-core computer security specialists will frown on creating passwords this way. They will always recommend passwords created from truly random strings of characters. I have encouraged you to create a recipe (i.e. algorithm) to generate strong passwords. Clever password crackers will, no doubt, develop dictionary attacks that mix common padding characters (i.e. “…”) with common words. Nevertheless, the solution I have proposed seems to me to be a good balance of security and usability.

Would not argue with those recommendations. You mention the need for a sufficiently long password so I’ll suggest that a current day absolute minimum of 9 characters and ideally more are necessary. If the suggestions presented here are followed however, that absolute minimum should be comfortably surpassed. Nice job.
Thanks Shawn. I will definitely share this with the family I support.